Distributed Denial of service [DDOS] attacks are popular cyber-attacks that focus on taking down a system’s availability by denying resources to legitimate connections. DDOS attacks can be found in many forms, commonly as an attack that heavily congests a network to the point of being unusable. Furthermore, DDoS attacks crash or even destroy resources depending on the robustness of the target system.
DDoS Attack Terminology
Agent – An agent is a node running a daemon.
Client – A client is an application that serves to send commands to daemons.
Daemon – A daemon is a process running on an agent which receives and executes commands issued by a client.
Master – A master is a node running the client.
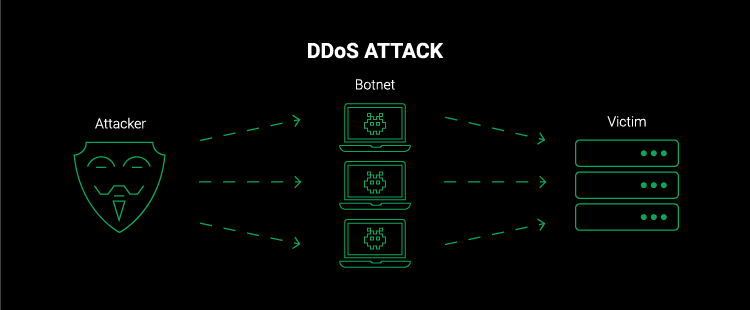
Botnet – A group of computers that have been infected by malware and are under the control of an attacker.
Denial of Service Attacks
DoS attacks reduce, restrict or prevent access to legitimate users. They are typically network attacks where malicious actors generate heavy traffic to consume bandwidth. Security experts categorize DoS based on their ability to deny service. Examples of DoS attacks are:
- Sending a victim massive amounts of traffic targeting a specific service.
- Crashing a TCP/IP stack by sending packets in an illegal state.
- Sending malicious traffic to cause system hangs or stalls.
- Interacting with a service in an unexpected way to generate a system crash.
Several techniques can enhance the effectiveness of DoS attacks. For Example:
- Adding more nodes to the attack.
- Amplifying the effect that each packet produces on the network.
Distribution
A distributed denial of service [DDOS] is a large-scale coordinated attack on a target’s network. A DDoS occurs when multiple systems in separate locations participate in a denial of service attack. By definition, DDoS attacks use more than one unique I.P. address. Often, they occur with thousands of distinct I.P.s. DDoS attacks most frequently come from a botnet. A botnet is a group of infected computers that execute arbitrary commands. A botnet owner sends messages from a master node to infected agents running daemon processes. When the command comes in, the agents will execute the order and send traffic of a given type to the specified target.
Techniques
A notable DoS technique is amplification. As its name suggests, amplification attacks make each node in the attack generate more packets than they are usually capable of. DoS amplification occurs when a node sends out one packet, producing more packets via other nodes. For example, sending a message to a broadcast address may result in all network-attached hosts receiving a packet as well. When performed as a DDoS attack, amplification is an effective force multiplier, resulting in massive traffic for improperly configured networks. Equally important, it reduces the burden of bandwidth consumption of the attacker, as the magnification occurs on nodes attackers don’t explicitly control.
Categories
Outlined below are four basic categories of DoS attacks.
Application attacks: Application DoS attacks go after the resources necessary for an application or service to run. If this type of attack is successful, the application will be unable to interact with legitimate users.
Fragmentation attacks: This attack takes advantage of weaknesses discovered in the underlying implementation of the TCP/IP protocol stack. Attackers send illegitimately constructed packet fragments to crash systems upon reconstruction.
Volumetric attacks: These attacks seek to congest a network beyond usability by eating up as much bandwidth as possible.
TCP state-exhaustion attacks: Exhaustion attacks seek to go after firewalls, load balancers, and the servers themselves by attempting to consume and tie up all available connection states.
Example DDoS Attacks
SYN flood: In a SYN flood attack, the attacker sends many SYN packets towards a target with no intention to respond to the SYN/ACK. Because there is a set amount of time the victim needs to wait before closing the connection, their resources are tied up waiting for a response. Consequently, when this happens at scale, the server will be unable to serve further connections.
Teardrop: For this attack, the victim is spammed with a massive amount of garbled I.P. fragments. These fragments are crafted in such a way as to generate overlapping and oversized payloads. As a result, the reassembly process defined by their TCP/IP stack on some operating systems fails, causing the system to crash.
DNS amplification: DNS amplification is a volumetric-based attack that seeks to leverage the functionality of DNS resolvers to overwhelm a target server with network traffic. It occurs when an attacker spoofs the victim’s I.P. address and sends out a significant number of DNS requests on the target’s behalf. Consequently, the DNS resolver then responds to these requests by sending a considerable amount of data to the victim. This may leave the network infrastructure so overwhelmed that it can no longer deal with authentic traffic.
Tools
In the next section, we will talk about popular and easily accessible tools that you can use in a lab environment to test out how DoS attacks work. Ensure that at no point in time do you point these tools at networks you do not control. Alternatively, ensure explicit written permission before using them in a test. Using any of the following tools on a system or network could be considered a felony under the Computer Fraud and Abuse Act of 1986.
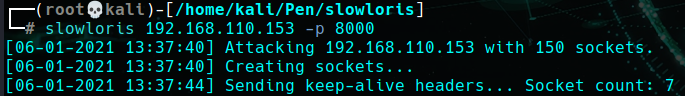
Slowloris
The Slowloris is a denial of service attack which aims to take down web servers. Its goal is to exhaust a machine’s resources while using minimal bandwidth. To demonstrate this attack, I am using Slowloris.py. This script fires multiple connections to a given target by sending partial HTTP request headers. For slow connections, it is not uncommon to receive partial headers over TCP/IP. Consequently, servers often have a grace period set before they time out a connection. As a result, Slowloris abuses this functionality by sending periodic headers for each connection. This keeps resources tied up indefinitely. To this end, the script never intends to close the connection, resulting in the exhaustion of the server’s thread pool. If servers aren’t configured to fight this attack, it will result in a denial of service to legitimate traffic.
Low Orbit Ion Cannon
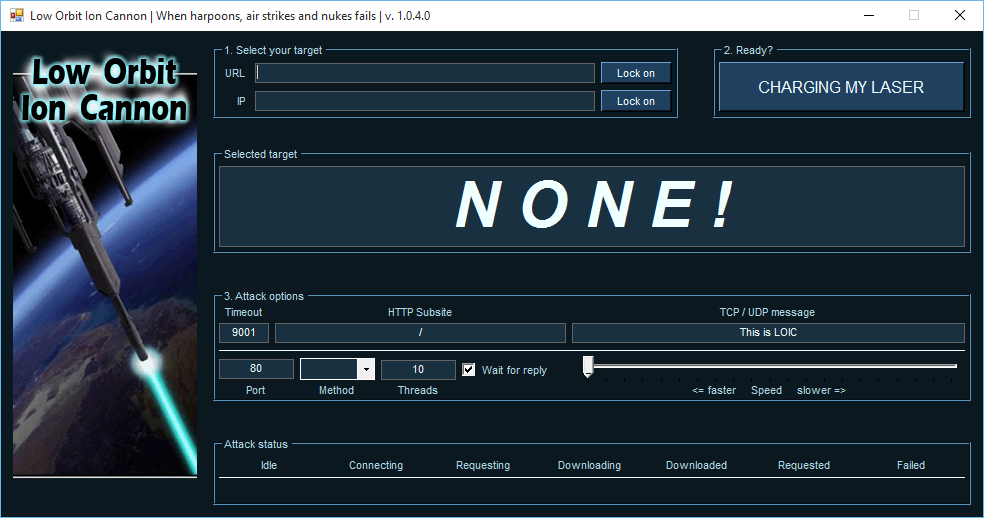
L.O.I.C. is an easy-to-use open-source stress tester for networks that will launch denial-of-service attacks. Written in C#, Praetox Technologies developed LOIC, later releasing it into the public domain. LOIC is notable for its use in Operation Payback by Anonymous back in December 2010 to attack websites and companies in opposition to WikiLeaks.
Operating LOIC is easy. Start by selecting a target for attack by entering the URL or I.P. address and clicking the Lock-on button. This should display the desired target. Next, verify it is correct and edit your attack options. Under these options, you can add additional data in the TCP / UDP data fields, set the speed you want the attack to run, and choose specific ports to attack. Simply maxing out the speed gauge is not always the best option depending on the ruleset of the target, so playing around with the parameters and watching the attack status can be effective in fine-tuning the attack. Finally, click ‘CHARGING MY LAZER’ to begin the DoS attack when you are ready. If you choose to run this in a home lab environment, you can usually see a noticeable degradation or all-out stop of a running service.
High Orbit Ion Cannon
H.O.I.C. was designed to be used as a DDoS tool where users could collaborate over an IRC channel to pick a target and launch an attack. It was intended to cause an HTTP Flood with as few a fifty users.
HOIC forgoes the use of malformed packets, spoofing, and amplification techniques altogether. Instead, it allows the application to directly target a site via malicious HTTP and POST requests. This lowers the outgoing bandwidth of a user to avoid throttling by an ISP while still degrading the performance of a remote application. With some clever reconnaissance, HOIC can spam GET requests for large static files such as images. Additionally, it can send an extensive amount of POST requests for resources that must be pulled from a database. HOIC can select up to 256 targets while utilizing multi-threading in its attacks. This, combined with the simplistic UI and booster files, makes it one of the more versatile tools for groups to carry out attacks.
R-U-Dead-Yet
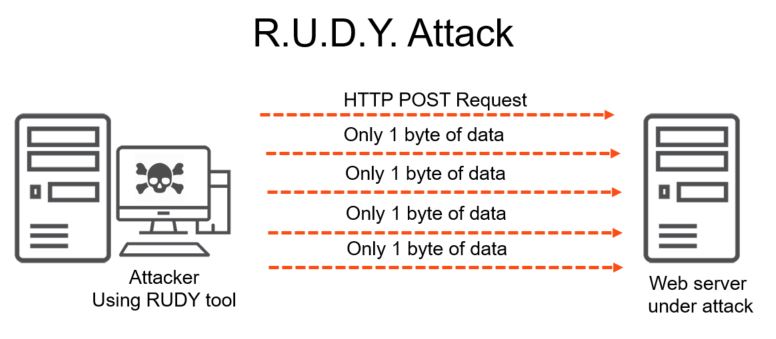
R.U.D.Y. is an OSI Layer 7 slow-rate attack that directs long-form fields to the target server. It is an abuse of the HTTP protocol, and its low traffic rate makes it very difficult to detect by much of the standard anti-DDoS mitigation software. RUDY sends an initial HTTP POST request followed by only one byte of data at random time intervals. Like the Slowloris attack, the server waits for the request to be completed and doesn’t time out due to the occasionally received byte. Since the tool doesn’t generate volumetric traffic, it is challenging to determine if a website is attacked by RUDY or simply hosting content for users with slow internet speeds.
Tribe Flood Network
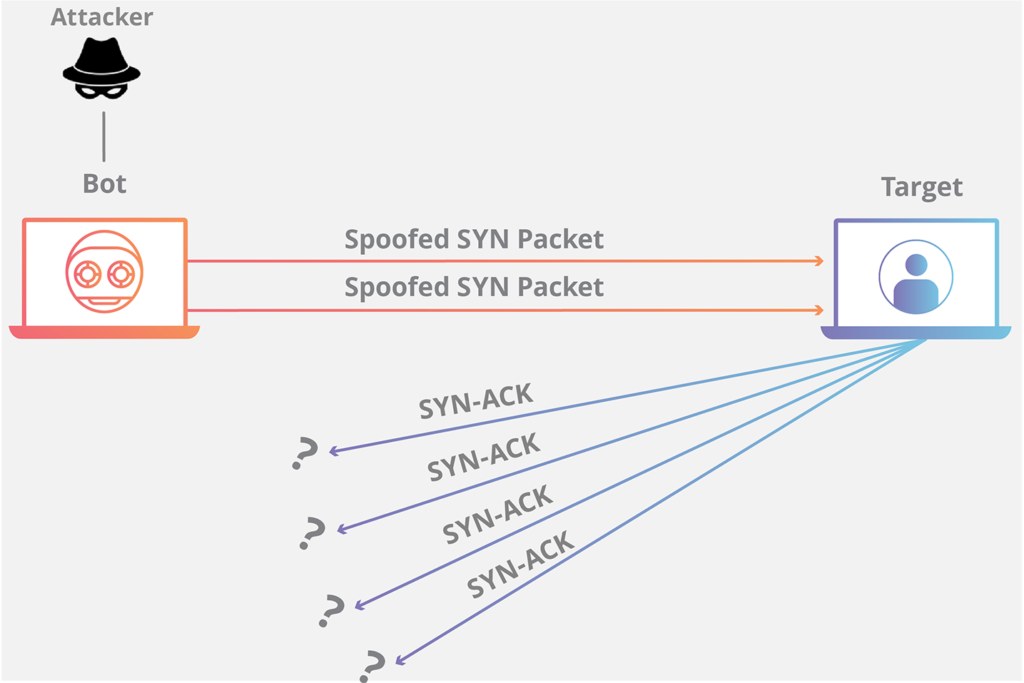
Tribe Flood Network [TFN] is a set of programs used to conduct various DDOS attacks such as ICMP, SYN, or UDP flooding. A TFN attack occurs when a TFN master station node sends out a command to its list of TFN servers. A TFN server is a node running the TFN daemon. Nodes running this software can generate packets with spoofed I.P. source addresses, and once they receive the command, they will start flooding the designated target. TFN nodes can randomize their source addresses and ports during an attack, making it difficult to detect. Additionally, the packet sizes sent over the wire can be of random variable length, making it harder to write a simple rule to filter the attack.
This program uses a distributed client/server architecture and various encryption methods to enhance its stealth capabilities. Analysts have broken down TFN into two components, a command-line driven client on the master node and installed daemon processes operating on agent nodes. The master coordinates the targets and gives the command to start, along with what type of attack to launch, and upon receiving the command, the agents will begin their attack. With Tribe, agent nodes wait for orders and don’t communicate anything to the master. As a result, attackers use master nodes over TCP, UDP, or ICMP with spoofed I.P. addresses. This makes it very difficult for white-hats to take down the master nodes running the botnet.
Conclusion
There are many other DDoS tools to play with, some of which are used for legitimate purposes. Often, developers use them to stress-test applications or load balancers to ensure robustness under duress. Some of these come in malware, such as trojans that connect unsuspecting nodes to a botnet as agents. Stacheldraht, Trinoo, Mirai, and 3ve come to mind for anyone who wants to continue to investigate. However, the fundamental concepts expressed here can be applied to most DDoS programs. Generally speaking, variations are noticeable within the infection mechanism or GUI Mirai, for example, is a botnet that took place in one of the most significant DDoS attacks of 2016 by brute-forcing IoT device passwords to gain recruits. This article aims to outline the primary concepts researchers will encounter and provide concrete examples and programs to get practical experience.



